20130827
20130825
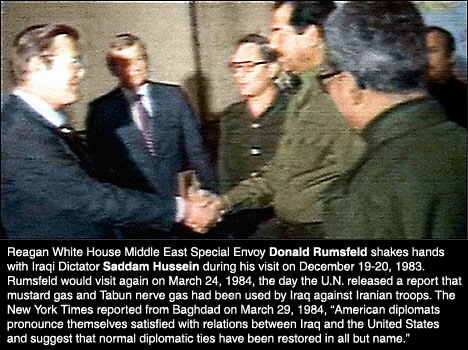
Exclusive: CIA Files Prove America Helped Saddam as He Gassed Iran
In 1988, during the waning days of Iraq's war with Iran, the United States learned through satellite imagery that Iran was about to gain a major strategic advantage by exploiting a hole in Iraqi defenses. U.S. intelligence officials conveyed the location of the Iranian troops to Iraq, fully aware that Hussein's military would attack with chemical weapons, including sarin, a lethal nerve agent.
The intelligence included imagery and maps about Iranian troop movements, as well as the locations of Iranian logistics facilities and details about Iranian air defenses. The Iraqis used mustard gas and sarin prior to four major offensives in early 1988 that relied on U.S. satellite imagery, maps, and other intelligence. These attacks helped to tilt the war in Iraq's favor and bring Iran to the negotiating table, and they ensured that the Reagan administration's long-standing policy of securing an Iraqi victory would succeed. But they were also the last in a series of chemical strikes stretching back several years that the Reagan administration knew about and didn't disclose...
Dead bees: More than 30 million found in Canada
Just weeks after tens of thousands of bumblebees, honeybees and lady bugs were found dead in an Oregon parking lot, more than 37 million bees have been found dead in Elmwood, Ontario, Canada, reports Collective Evolution.
As scientists struggle to find the cause of the massive die-offs, a phenomenon they call “colony collapse disorder,” Elmwood beekeeper Dave Schuit is pointing the finger at neonicotinoid pesticides. Schuit lost 600 hives.
Research suggests that even at nonlethal does, the world’s most popular class of pesticides can confuse bees’ navigation and make it hard for them to find home.
After a record-breaking loss of honeybees in the United Kingdom, the European Union hasbanned multiple pesticides, including neonicotinoid pesticides...
As scientists struggle to find the cause of the massive die-offs, a phenomenon they call “colony collapse disorder,” Elmwood beekeeper Dave Schuit is pointing the finger at neonicotinoid pesticides. Schuit lost 600 hives.
Research suggests that even at nonlethal does, the world’s most popular class of pesticides can confuse bees’ navigation and make it hard for them to find home.
After a record-breaking loss of honeybees in the United Kingdom, the European Union hasbanned multiple pesticides, including neonicotinoid pesticides...
20130824
September 1, 2000: A pocket guide to NSA sabotage
The NSA engages in sabotage, much of it against American companies and products. One campaign apparently occurred at about the time when PGP's most serious vulnerability was added.
To understand the whole story requires some background.
In Bruce Schneier's newsletter Crypto-Gram he told us last year about Lew Giles, said to be an NSA saboteur wrecking American privacy products in 1997. Schneier says that according to several sources Giles went from company to company, asking them to destroy the security of their own products, and arranging cover stories to protect them. According to Crypto-Gram sometimes Giles worked directly with engineers, with no managers around. The sabotage was always supposed to look like a mistake. At about the same time, PGP introduced "key recovery" with the hidden flaw recently covered worldwide, including Schneier's own clear description in Slashdot.
Other serious vulnerabilities have been found in the PGP versions released then. For example, just last May PGP was found to generate weak keys on Linux and OpenBSD. The original report in BugTraq says the bug was introduced in version 5.0, released in 1997... http://cryptome.org/nsa-sabotage.htm
In Bruce Schneier's newsletter Crypto-Gram he told us last year about Lew Giles, said to be an NSA saboteur wrecking American privacy products in 1997. Schneier says that according to several sources Giles went from company to company, asking them to destroy the security of their own products, and arranging cover stories to protect them. According to Crypto-Gram sometimes Giles worked directly with engineers, with no managers around. The sabotage was always supposed to look like a mistake. At about the same time, PGP introduced "key recovery" with the hidden flaw recently covered worldwide, including Schneier's own clear description in Slashdot.
Other serious vulnerabilities have been found in the PGP versions released then. For example, just last May PGP was found to generate weak keys on Linux and OpenBSD. The original report in BugTraq says the bug was introduced in version 5.0, released in 1997... http://cryptome.org/nsa-sabotage.htm
20130821
FBI resists thorough search of vast 9/11 files in Tampa for records about Sarasota Saudis
A mass of documents detailing the Tampa area connection to the 9/11 attacks on New York and Washington, many of which may have never been made public, are stored out of sight in the FBI’s Tampa field office.
“The FBI’s Tampa office alone has more than 15,352 documents (serials), which together contain, potentially, hundreds of thousands of pages of records related to the 9/11 investigation,” say new court papers filed by the U.S. Department of Justice in federal court in Fort Lauderdale.
Precisely what information is contained in those records was not disclosed.
The Justice Department cited the Tampa records in an effort to convince U.S. District Judge William Zloch not to order the FBI to conduct a more thorough search for records of its investigation into apparent ties between the 9/11 hijackers, including ringleader Mohamed Atta, and Saudis living in Sarasota...
http://www.browardbulldog.org/2013/08/fbi-resists-thorough-search-of-vast-911-files-in-tampa-for-records-about-sarasota-saudis/
“The FBI’s Tampa office alone has more than 15,352 documents (serials), which together contain, potentially, hundreds of thousands of pages of records related to the 9/11 investigation,” say new court papers filed by the U.S. Department of Justice in federal court in Fort Lauderdale.
Precisely what information is contained in those records was not disclosed.
The Justice Department cited the Tampa records in an effort to convince U.S. District Judge William Zloch not to order the FBI to conduct a more thorough search for records of its investigation into apparent ties between the 9/11 hijackers, including ringleader Mohamed Atta, and Saudis living in Sarasota...
http://www.browardbulldog.org/2013/08/fbi-resists-thorough-search-of-vast-911-files-in-tampa-for-records-about-sarasota-saudis/
US Government Protection of Al-Qaeda Terrorists and the US-Saudi Black Hole
For almost two centuries American government, though always imperfect, was also a model for the world of limited government, having evolved a system of restraints on executive power through its constitutional arrangement of checks and balances.
Since 9/11 however, constitutional practices have been overshadowed by a series of emergency measures to fight terrorism. The latter have mushroomed in size, reach and budget, while traditional government has shrunk. As a result we have today what the journalist Dana Priest has called two governments: the one its citizens were familiar with, operated more or less in the open: the other a parallel top secret government whose parts had mushroomed in less than a decade into a gigantic, sprawling universe of its own, visible to only a carefully vetted cadre – and its entirety…visible only to God.1
More and more, it is becoming common to say that America, like Turkey before it, now has what Marc Ambinder and John Tirman have called a deep state behind the public one.2 And this parallel government is guided in surveillance matters by its own Foreign Intelligence Surveillance Court, known as the FISA court, which according to the New York Times, “has quietly become almost a parallel Supreme Court.”3 Thanks largely to Edward Snowden, it is now clear that the FISA Court has permitted this deep state to expand surveillance beyond the tiny number of known and suspected Islamic terrorists, to any incipient protest movement that might challenge the policies of the American war machine...
Since 9/11 however, constitutional practices have been overshadowed by a series of emergency measures to fight terrorism. The latter have mushroomed in size, reach and budget, while traditional government has shrunk. As a result we have today what the journalist Dana Priest has called two governments: the one its citizens were familiar with, operated more or less in the open: the other a parallel top secret government whose parts had mushroomed in less than a decade into a gigantic, sprawling universe of its own, visible to only a carefully vetted cadre – and its entirety…visible only to God.1
More and more, it is becoming common to say that America, like Turkey before it, now has what Marc Ambinder and John Tirman have called a deep state behind the public one.2 And this parallel government is guided in surveillance matters by its own Foreign Intelligence Surveillance Court, known as the FISA court, which according to the New York Times, “has quietly become almost a parallel Supreme Court.”3 Thanks largely to Edward Snowden, it is now clear that the FISA Court has permitted this deep state to expand surveillance beyond the tiny number of known and suspected Islamic terrorists, to any incipient protest movement that might challenge the policies of the American war machine...
5 Companies That Make Money By Keeping Americans Terrified of Terror Attacks
Michael Hayden, the former director of the National Security Agency, has invaded America’s television sets in recent weeks to warn about Edward Snowden’s leaks and the continuing terrorist threat to America.
But what often goes unmentioned, as the Guardian’s Glenn Greenwald pointed out, is that Hayden has a financial stake in keeping Americans scared and on a permanent war footing against Islamist militants. And the private firm he works for, called the Chertoff Group, is not the only one making money by scaring Americans.
Post-9/11 America has witnessed a boom in private firms dedicated to the hyped-up threat of terrorism. The drive to privatize America's national security apparatus accelerated in the aftermath of the terrorist attacks, and it’s gotten to the point where 70 percent of the national intelligence budget is now spent on private contractors, as author Tim Shorrock reported. The private intelligence contractors have profited to the tune of at least $6 billion a year. In 2010, the Washington Post revealed that there are 1,931 private firms across the country dedicated to fighting terrorism...
http://www.alternet.org/civil-liberties/5-companies-make-money-keeping-americans-terrified-terror-attacks
But what often goes unmentioned, as the Guardian’s Glenn Greenwald pointed out, is that Hayden has a financial stake in keeping Americans scared and on a permanent war footing against Islamist militants. And the private firm he works for, called the Chertoff Group, is not the only one making money by scaring Americans.
Post-9/11 America has witnessed a boom in private firms dedicated to the hyped-up threat of terrorism. The drive to privatize America's national security apparatus accelerated in the aftermath of the terrorist attacks, and it’s gotten to the point where 70 percent of the national intelligence budget is now spent on private contractors, as author Tim Shorrock reported. The private intelligence contractors have profited to the tune of at least $6 billion a year. In 2010, the Washington Post revealed that there are 1,931 private firms across the country dedicated to fighting terrorism...
http://www.alternet.org/civil-liberties/5-companies-make-money-keeping-americans-terrified-terror-attacks
Time for Answers from the NSA
It’s time to ask tough questions about the National Security Agency’s surveillance activities — even for conservatives who have given the NSA the benefit of every doubt up until now.
The Washington Post opened a can of worms last Friday when it reported that, in 2012, an internal NSA audit found that the agency had violated privacy rules 2,776 times within just one year. The audit counted only violations at NSA’s Washington facilities — nearly 20 other NSA facilities were not included. In the wake of the Post’s report, the NSA insisted that the violations were “inadvertent,” but it failed to explain why it had not shared the report with Senate Intelligence Committee chair Dianne Feinstein or other congressional oversight authorities.
Yet some NSA defenders continue to insist that nothing is wrong. Back in July, House Intelligence Committee chair Mike Rogers claimed that there have been “zero privacy violations” on the part of NSA. After the leaked audit made news on Friday, he retreated to saying that “there was no intentional and willful violation of the law...”
The Washington Post opened a can of worms last Friday when it reported that, in 2012, an internal NSA audit found that the agency had violated privacy rules 2,776 times within just one year. The audit counted only violations at NSA’s Washington facilities — nearly 20 other NSA facilities were not included. In the wake of the Post’s report, the NSA insisted that the violations were “inadvertent,” but it failed to explain why it had not shared the report with Senate Intelligence Committee chair Dianne Feinstein or other congressional oversight authorities.
Yet some NSA defenders continue to insist that nothing is wrong. Back in July, House Intelligence Committee chair Mike Rogers claimed that there have been “zero privacy violations” on the part of NSA. After the leaked audit made news on Friday, he retreated to saying that “there was no intentional and willful violation of the law...”
20130819
PROTON, CLEARWATER and Lexis-Nexis
"Given the use of constitutionally repulsive practices by the Department of Justice, the Internal Revenue Service and other federal agencies, this information is being made public to educate and inform so they might arm themselves against government intrusion and for attorneys as a backgrounder for future appeals.
I suggest American guerillas seek non-Internet modes of communication. If you think Rex Sherwood was pulled over for not using a turn signal, you are wrong.
I was "read on" the PROTON/CRISSCROSS program in late 2006 and was a frequent user of this system for over a year. As part of my duties, I employed PROTON/CRISSCROSS in HUMINT exploitation role. In the Intelligence Community, PROTON/CRISSCROSS is referred to as PROTON. Unless otherwise specified, the same is true in this report.
PROTON is a storage and analysis system of telecommunications selectors at the TS/SI/FISA/ORCON/NOFORN level of classification and handling. PROTON is the program name as well as the name of the technology. It has been described as "SAP-like", and I suspect that PROTON was once a DEA special program. PROTON is well known in HUMINT and DOJ clandestine law enforcement. It remains the primary, if not fundamental, tool of HUMINT and DOJ law enforcement operations, both of which have considerable overlap in phenomenology and methodology. PROTON carries the FISA caveat because Top Secret FISA collection is contained in PROTON's massive database..."
http://cryptome.org/2013/08/proton-clearwater-lexis-nexis.htm
I suggest American guerillas seek non-Internet modes of communication. If you think Rex Sherwood was pulled over for not using a turn signal, you are wrong.
I was "read on" the PROTON/CRISSCROSS program in late 2006 and was a frequent user of this system for over a year. As part of my duties, I employed PROTON/CRISSCROSS in HUMINT exploitation role. In the Intelligence Community, PROTON/CRISSCROSS is referred to as PROTON. Unless otherwise specified, the same is true in this report.
PROTON is a storage and analysis system of telecommunications selectors at the TS/SI/FISA/ORCON/NOFORN level of classification and handling. PROTON is the program name as well as the name of the technology. It has been described as "SAP-like", and I suspect that PROTON was once a DEA special program. PROTON is well known in HUMINT and DOJ clandestine law enforcement. It remains the primary, if not fundamental, tool of HUMINT and DOJ law enforcement operations, both of which have considerable overlap in phenomenology and methodology. PROTON carries the FISA caveat because Top Secret FISA collection is contained in PROTON's massive database..."
http://cryptome.org/2013/08/proton-clearwater-lexis-nexis.htm
CIA Confirms Role in 1953 Iran Coup
Documents Provide New Details on Mosaddeq Overthrow and Its Aftermath...
Fukushima apocalypse: Years of ‘duct tape fixes’ could result in ‘millions of deaths’
Even the tiniest mistake during an operation to extract over 1,300 fuel rods at the crippled Fukushima nuclear power plant in Japan could lead to a series of cascading failures with an apocalyptic outcome, fallout researcher Christina Consolo told RT.
Fukushima operator TEPCO wants to extract 400 tons worth of spent fuel rods stored in a pool at the plant’s damaged Reactor No. 4. The removal would have to be done manually from the top store of the damaged building in the radiation-contaminated environment.
In the worst-case scenario, a mishandled rod may go critical, resulting in an above-ground meltdown releasing radioactive fallout with no way to stop it, said Consolo, who is the founder and host of Nuked Radio. But leaving the things as they are is not an option, because statistical risk of a similarly bad outcome increases every day, she said....
...- The process of removing each rod will have to be repeated over 1,300 times without incident...
http://rt.com/news/fukushima-apocalypse-fuel-removal-598/
In the worst-case scenario, a mishandled rod may go critical, resulting in an above-ground meltdown releasing radioactive fallout with no way to stop it, said Consolo, who is the founder and host of Nuked Radio. But leaving the things as they are is not an option, because statistical risk of a similarly bad outcome increases every day, she said....
...- The process of removing each rod will have to be repeated over 1,300 times without incident...
http://rt.com/news/fukushima-apocalypse-fuel-removal-598/
20130818
JPMorgan hiring in China being investigated
Authorities are investigating whether JPMorgan Chase's Chinese offices hired young workers from prominent Chinese families that in turn offered the bank business.
The bank made a passing reference to a Securities and Exchange Commission investigation in its quarterly filing earlier this month, and The New York Times fanned the fire by reporting on a confidential U.S. government document that went into greater detail.
The document showed that the SEC is looking into the hiring of several well-connected young JPMorgan (JPM, Fortune 500) employees, including the son of the former vice chairman of China's top banking regulator and the daughter of a Chinese railway official, according to the Times...
http://money.cnn.com/2013/08/18/news/companies/jpmorgan-investigation-china/index.html
The document showed that the SEC is looking into the hiring of several well-connected young JPMorgan (JPM, Fortune 500) employees, including the son of the former vice chairman of China's top banking regulator and the daughter of a Chinese railway official, according to the Times...
http://money.cnn.com/2013/08/18/news/companies/jpmorgan-investigation-china/index.html
This is Your Brain on Terrorism
Edward Snowden’s revelations about the federal government’s mass collection of phone records, emails, web browsing history and social media interactions have prompted a collective contemplation of a critical question: Should we surrender Constitutionally-enshrined liberties for the government’s promise of security against terror?
Unfortunately, our ability to reach a rational decision on this question is hampered by our humanity: While the homo sapiens brain has come a long way, it’s still wired to assess potential threats with emotion rather than reason.As a result, we’re susceptible to extreme exaggeration of the threat of terrorism and may be making a catastrophically bad bargain with our essential freedoms.
Our Lizard Brains: Wired for Snakes...
http://libertymcg.com/2013/07/23/this-is-your-brain-on-terrorism/
http://libertymcg.com/2013/07/23/this-is-your-brain-on-terrorism/
20130815
NSA broke privacy rules thousands of times per year, audit finds
The National Security Agency has broken privacy rules or overstepped its legal authority thousands of times each year since Congress granted the agency broad new powers in 2008, according to an internal audit and other top-secret documents.
Most of the infractions involve unauthorized surveillance of Americans or foreign intelligence targets in the United States, both of which are restricted by statute and executive order. They range from significant violations of law to typographical errors that resulted in unintended interception of U.S. e-mails and telephone calls.
The documents, provided earlier this summer to The Washington Post by former NSA contractor Edward Snowden, include a level of detail and analysis that is not routinely shared with Congress or the special court that oversees surveillance. In one of the documents, agency personnel are instructed to remove details and substitute more generic language in reports to the Justice Department and the Office of the Director of National Intelligence.
In one instance, the NSA decided that it need not report the unintended surveillance of Americans. A notable example in 2008 was the interception of a “large number” of calls placed from Washington when a programming error confused the U.S. area code 202 for 20, the international dialing code for Egypt, according to a “quality assurance” review that was not distributed to the NSA’s oversight staff...
http://www.washingtonpost.com/world/national-security/nsa-broke-privacy-rules-thousands-of-times-per-year-audit-finds/2013/08/15/3310e554-05ca-11e3-a07f-49ddc7417125_print.html
XScoreKey: Network Radar Deja Vu
"From: Todd Heberlein <todd_heberlein@mac.com>
To: To: Fed Talk <Fed-talk@lists.apple.com>
Subject: [Fed-Talk] It began on a NeXT
Date: August 15, 2013 1:45 PM
To: To: Fed Talk <Fed-talk@lists.apple.com>
Subject: [Fed-Talk] It began on a NeXT
Date: August 15, 2013 1:45 PM
I put together a 10 minute video comparing a recently revealed government system to my old Network Radar system I developed in the 1990s. Not any Mac-ness in it, but I did start development of Network Radar on my own on a NeXT (OS X's parent) in 1995. I loved that machine.
At the end I tacked on the cluster activity as the ILOVEYOU worm hits Rome Labs in 13 years ago. It might be fun for anyone at AFRL.
http://www.netsq.com/Podcasts/Data/2013/XScoreKeyDejaVu/
Todd
PS. I subconsciously mangled the government's system name because I cannot pronounce the actual name out loud without mangling it. I challenge you to pronounce it 3 times fast..."
http://www.netsq.com/Podcasts/Data/2013/XScoreKeyDejaVu/
At the end I tacked on the cluster activity as the ILOVEYOU worm hits Rome Labs in 13 years ago. It might be fun for anyone at AFRL.
http://www.netsq.com/Podcasts/Data/2013/XScoreKeyDejaVu/
Todd
PS. I subconsciously mangled the government's system name because I cannot pronounce the actual name out loud without mangling it. I challenge you to pronounce it 3 times fast..."
http://www.netsq.com/Podcasts/Data/2013/XScoreKeyDejaVu/
20130814
Japanese WWII Torture Document Eerily Reminiscent of US Torture Program
The following is taken from a 63 year old book published in the early days of the Cold War. Titled Materials on the Trial of Former Serviceman of the Japanese Army Charged with Manufacturing and Employing Bacteriological Weapons(Foreign Languages Publishing House, Moscow, 1950), the book contains trial summaries and testimony from the Khabarovsk war crimes trial in December 1949.
Derided as just another Stalinist show trial at the time, historians have since confirmed the evidence regarding the crimes prosecuted, including deadly biological experiments on prisoners by special units of the Japanese Imperial Army, the most famous of which was Unit 731.
The selection below is one of the exhibits contained in the book, collected in a section labeled “Documentary Evidence.” The book itself has been out of print for decades, and is generally unavailable, except via some few libraries and antiquarian bookstores. The selection included here is on the Japanese Army use of torture. The reader will notice that the Japanese Army demonstrated many of the same techniques and concerns the U.S. showed when it was implementing its own torture program under the CIA and the Department of Defense...
http://valtinsblog.blogspot.com/2013/08/japanese-wwii-torture-document-eerily.html
Derided as just another Stalinist show trial at the time, historians have since confirmed the evidence regarding the crimes prosecuted, including deadly biological experiments on prisoners by special units of the Japanese Imperial Army, the most famous of which was Unit 731.
The selection below is one of the exhibits contained in the book, collected in a section labeled “Documentary Evidence.” The book itself has been out of print for decades, and is generally unavailable, except via some few libraries and antiquarian bookstores. The selection included here is on the Japanese Army use of torture. The reader will notice that the Japanese Army demonstrated many of the same techniques and concerns the U.S. showed when it was implementing its own torture program under the CIA and the Department of Defense...
http://valtinsblog.blogspot.com/2013/08/japanese-wwii-torture-document-eerily.html
20130811
Bugger
The recent revelations by the whistleblower Edward Snowden were fascinating. But they - and all the reactions to them - had one enormous assumption at their heart.
That the spies know what they are doing.
It is a belief that has been central to much of the journalism about spying and spies over the past fifty years. That the anonymous figures in the intelligence world have a dark omniscience. That they know what's going on in ways that we don't.
It doesn't matter whether you hate the spies and believe they are corroding democracy, or if you think they are the noble guardians of the state. In both cases the assumption is that the secret agents know more than we do...
20130809
The Cops Can Take Away Your Cash, Car, Or House
The New Yorker's Sarah Stillman has a heartbreaking story out on an appalling police tactic — civil forfeiture, which lets local police departments make tons of money from taking supposed criminals' property.
Civil forfeiture is largely a product of the war on drugs. In 1984, Congress passed an omnibus crime bill that gave local police departments a cut of the assets seized during drug raids and other investigations.
Through civil forfeiture, cops can take property they believe was obtained illicitly before you're convicted of any wrongdoing in a court of law. The people whose assets have been seized then have to go to court to try to get it back, which may cost more money than the property itself.
http://www.businessinsider.com/new-yorker-article-on-civil-forfeiture-2013-8#ixzz2bSVDdYDP
Civil forfeiture is largely a product of the war on drugs. In 1984, Congress passed an omnibus crime bill that gave local police departments a cut of the assets seized during drug raids and other investigations.
Through civil forfeiture, cops can take property they believe was obtained illicitly before you're convicted of any wrongdoing in a court of law. The people whose assets have been seized then have to go to court to try to get it back, which may cost more money than the property itself.
http://www.businessinsider.com/new-yorker-article-on-civil-forfeiture-2013-8#ixzz2bSVDdYDP
20130808
NSA cites case as success of phone data-collection program
He was a San Diego cab driver who fled Somalia as a teenager, winning asylum in the United States after he was wounded during fighting among warring tribes. Today, Basaaly Moalin, 36, is awaiting sentencing following his conviction on charges that he sent $8,500 to Somalia in support of the terrorist group al-Shabab.
Moalin’s prosecution, barely noticed when the case was in court, has suddenly come to the fore of a national debate about U.S. surveillance. Under pressure from Congress, senior intelligence officials have offered it as their primary example of the unique value of a National Security Agency program that collects tens of millions of phone records from Americans.
Officials have said that NSA surveillance tools have helped disrupt terrorist plots or identify suspects in 54 cases in the United States and overseas. In many of those cases, an agency program that targets the communication of foreigners, including e-mails, has proved critical...
http://www.washingtonpost.com/world/national-security/nsa-cites-case-as-success-of-phone-data-collection-program/2013/08/08/fc915e5a-feda-11e2-96a8-d3b921c0924a_print.html
Moalin’s prosecution, barely noticed when the case was in court, has suddenly come to the fore of a national debate about U.S. surveillance. Under pressure from Congress, senior intelligence officials have offered it as their primary example of the unique value of a National Security Agency program that collects tens of millions of phone records from Americans.
Officials have said that NSA surveillance tools have helped disrupt terrorist plots or identify suspects in 54 cases in the United States and overseas. In many of those cases, an agency program that targets the communication of foreigners, including e-mails, has proved critical...
http://www.washingtonpost.com/world/national-security/nsa-cites-case-as-success-of-phone-data-collection-program/2013/08/08/fc915e5a-feda-11e2-96a8-d3b921c0924a_print.html
20130807
Connections Between Michael Hastings, Edward Snowden And Barrett Brown—The War With The Security State
Any probe into Hastings’s untimely death needs to take into account this complex but essential background...
http://whowhatwhy.com/2013/08/07/connections-between-michael-hastings-edward-snowden-and-barrett-brown-the-war-with-the-security-state/
Nicknames and Codewords
Below is a listing of nicknames and codewords related to US Signals Intelligence (SIGINT) and Communications Security (COMSEC). Most of them are from the NSA, some are from other government or military agencies. Due to secrecy, it's not always clear whether a word is a nickname or a codeword. Some of them also have an abbreviation which is shown in brackets.
Nicknames are generally unclassified. NSA uses single word nicknames, outside NSA they usually consist of two separate words, with the first word selected from alphabetical blocks that are assigned to different agencies by the Joint Staff. Usually, nicknames are printed using all capital letters.
Codewords are always classified and always consist of a single word. Active codewords always need to be shown together with their classification level. Normally, codewords are printed using all capital letters....
http://electrospaces.blogspot.com/p/nicknames-and-codewords.html
Nicknames are generally unclassified. NSA uses single word nicknames, outside NSA they usually consist of two separate words, with the first word selected from alphabetical blocks that are assigned to different agencies by the Joint Staff. Usually, nicknames are printed using all capital letters.
Codewords are always classified and always consist of a single word. Active codewords always need to be shown together with their classification level. Normally, codewords are printed using all capital letters....
http://electrospaces.blogspot.com/p/nicknames-and-codewords.html
20130806
Obama's abuse of the Espionage Act is modern-day McCarthyism
The conviction of Bradley Manning under the 1917 Espionage Act, and the US Justice Department's decision to file espionage charges againstNSA whistleblower Edward Snowden under the same act, are yet further examples of the Obama administration's policy of using an iron fist against human rights and civil liberties activists.
President Obama has been unprecedented in his use of the Espionage Act to prosecute those whose whistleblowing he wants to curtail. The purpose of an Espionage Act prosecution, however, is not to punish a person for spying for the enemy, selling secrets for personal gain, or trying to undermine our way of life. It is to ruin the whistleblower personally, professionally and financially. It is meant to send a message to anybody else considering speaking truth to power: challenge us and we will destroy you.
Only ten people in American history have been charged with espionage for leaking classified information, seven of them under Barack Obama. The effect of the charge on a person's life – being viewed as a traitor, being shunned by family and friends, incurring massive legal bills – is all a part of the plan to force the whistleblower into personal ruin, to weaken him to the point where he will plead guilty to just about anything to make the case go away. I know. The three espionage charges against me made me one of "the Obama Seven"...
http://www.theguardian.com/commentisfree/2013/aug/06/obama-abuse-espionage-act-mccarthyism
President Obama has been unprecedented in his use of the Espionage Act to prosecute those whose whistleblowing he wants to curtail. The purpose of an Espionage Act prosecution, however, is not to punish a person for spying for the enemy, selling secrets for personal gain, or trying to undermine our way of life. It is to ruin the whistleblower personally, professionally and financially. It is meant to send a message to anybody else considering speaking truth to power: challenge us and we will destroy you.
Only ten people in American history have been charged with espionage for leaking classified information, seven of them under Barack Obama. The effect of the charge on a person's life – being viewed as a traitor, being shunned by family and friends, incurring massive legal bills – is all a part of the plan to force the whistleblower into personal ruin, to weaken him to the point where he will plead guilty to just about anything to make the case go away. I know. The three espionage charges against me made me one of "the Obama Seven"...
http://www.theguardian.com/commentisfree/2013/aug/06/obama-abuse-espionage-act-mccarthyism
Snow Job: U.S. Air Force Flies Cocaine from Costa Rica to Miami
A curious cargo airlift operation recently took place at the Daniel Oduber Quiros International Airport (LIR), in the northern province of Guanacaste. According to a news report by Alvaro Sanchez from online news daily CRHoy, nearly 24 tons of cocaine were loaded onto a United States Air Force transport aircraft. The destination of the controversial payload? Miami, a city that once held the infamous title of “Cocaine Capital of the World.”
The public affairs office of the Organization of Judicial Investigations (OIJ in Spanish) in Costa Rica explained to CRHoy that the 23 tons and 780 kilograms of powder cocaine hydrochloride were the result of two years of interdiction work by the National Coast Guard Service, the OIJ, the Border Police, and Fuerza Publica (the national police force in Costa Rica). This does not include seizures made by the U.S. Coast Guard and U.S. Navy as part of the Joint Patrol Agreement between Costa Rica and the U.S.
http://news.co.cr/snow-job-u-s-air-force-flies-cocaine-from-costa-rica-to-miami/23936/
The public affairs office of the Organization of Judicial Investigations (OIJ in Spanish) in Costa Rica explained to CRHoy that the 23 tons and 780 kilograms of powder cocaine hydrochloride were the result of two years of interdiction work by the National Coast Guard Service, the OIJ, the Border Police, and Fuerza Publica (the national police force in Costa Rica). This does not include seizures made by the U.S. Coast Guard and U.S. Navy as part of the Joint Patrol Agreement between Costa Rica and the U.S.
http://news.co.cr/snow-job-u-s-air-force-flies-cocaine-from-costa-rica-to-miami/23936/
No shooting at protest? Police may block mobile devices via Apple
Apple has patented a piece of technology which would allow government and police to block transmission of information, including video and photographs, from any public gathering or venue they deem “sensitive”, and “protected from externalities.”
In other words, these powers will have control over what can and cannot be documented on wireless devices during any public event.
And while the company says the affected sites are to be mostly cinemas, theaters, concert grounds and similar locations, Apple Inc. also says “covert police or government operations may require complete ‘blackout’ conditions.”
“Additionally,” Apple says,” the wireless transmission of sensitive information to a remote source is one example of a threat to security. This sensitive information could be anything from classified government information to questions or answers to an examination administered in an academic setting.”
http://rt.com/news/apple-patent-transmission-block-408/
In other words, these powers will have control over what can and cannot be documented on wireless devices during any public event.
And while the company says the affected sites are to be mostly cinemas, theaters, concert grounds and similar locations, Apple Inc. also says “covert police or government operations may require complete ‘blackout’ conditions.”
“Additionally,” Apple says,” the wireless transmission of sensitive information to a remote source is one example of a threat to security. This sensitive information could be anything from classified government information to questions or answers to an examination administered in an academic setting.”
http://rt.com/news/apple-patent-transmission-block-408/
T.S.A. Expands Duties Beyond Airport Security
WASHINGTON — As hundreds of commuters emerged from Amtrak and commuter trains at Union Station on a recent morning, an armed squad of men and women dressed in bulletproof vests made their way through the crowds.
The squad was not with the Washington police department or Amtrak’s police force, but was one of the Transportation Security Administration’s Visible Intermodal Prevention and Response squads — VIPR teams for short — assigned to perform random security sweeps to prevent terrorist attacks at transportation hubs across the United States.
“The T.S.A., huh,” said Donald Neubauer of Greenville, Ohio, as he walked past the squad. “I thought they were just at the airports...”
20130805
Charles Varnadore, Whistle-Blower at Lab, Dies at 71
After Charles D. Varnadore complained about safety at the Oak Ridge National Laboratory in Tennessee, where he worked as a technician, his bosses moved him to an office containing radioactive waste. When an industrial hygienist recommended that either he or the waste be moved, he was put in a room contaminated with mercury.
Mr. Varnadore fought back, publicizing questionable safety practices at Oak Ridge, a federal nuclear research center that had helped develop the atomic bomb, and his own treatment, which he characterized as retaliation for his outspokenness.
His complaints drew national attention, and he found allies in the federal government...
His complaints drew national attention, and he found allies in the federal government...
20130804
Hollywood freely collaborated with Hitler and China is next.
Such alarming revelations, many based on newly unearthed documents, are the basis of Harvard scholar Ben Urwand’s new book, “The Collaboration: Hollywood’s Pact with Hitler.” Urwand notes that 1930s Berlin heavily censored movies out of Hollywood, which would not deliver a major anti-Hitler production until 1939.
Hollywood effectively submitted its films for approval to Georg Gyssling, a Nazi diplomat who arrived in LA in 1931 and threatened the studios with “Article 15,” which said that if an American film released anywhere in the world offended Germany, the Germans would ban all other releases from the same studio...
http://www.nypost.com/p/news/opinion/opedcolumnists/shanghaied_CDRl1DbGRu5DjclErtYYhL
US regulators 'find evidence' of banks fixing derivative rates.
The Commodity Futures Trading Commission (CFTC) is probing 15 banks over allegations that they instructed brokers to carry out trades that would move ISDAfix, the leading benchmark rate for interest rate swaps.
Pension funds and companies who invest in interest rate derivatives often deal with banks to insure against big movements in the ISDAfix rate or to speculate on changes to interest rate swaps
ISDAfix is published each morning after banks submit bids for swaps via Icap, the inter-dealer broker, in a number of currencies. The CFTC has been investigating suggestions that the banks deliberately moved the rate in order to profit on these deals.
http://www.telegraph.co.uk/finance/newsbysector/banksandfinance/10219333/US-regulators-find-evidence-of-banks-fixing-derivative-rates.html
Pension funds and companies who invest in interest rate derivatives often deal with banks to insure against big movements in the ISDAfix rate or to speculate on changes to interest rate swaps
ISDAfix is published each morning after banks submit bids for swaps via Icap, the inter-dealer broker, in a number of currencies. The CFTC has been investigating suggestions that the banks deliberately moved the rate in order to profit on these deals.
http://www.telegraph.co.uk/finance/newsbysector/banksandfinance/10219333/US-regulators-find-evidence-of-banks-fixing-derivative-rates.html
20130801
Update: Now We Know Why Googling 'Pressure Cookers' Gets a Visit from Cops
Michele Catalano was looking for information online about pressure cookers. Her husband, in the same time frame, was Googling backpacks. Wednesday morning, six men from a joint terrorism task force showed up at their house to see if they were terrorists. Which prompts the question: How'd the government know what they were Googling?
Update, 7:05 p.m.: Because the Googling happened at work.
The Suffolk County Police Department released a statement this evening that answers the great mystery of the day...
http://www.theatlanticwire.com/national/2013/08/government-knocking-doors-because-google-searches/67864/
Update, 7:05 p.m.: Because the Googling happened at work.
The Suffolk County Police Department released a statement this evening that answers the great mystery of the day...
http://www.theatlanticwire.com/national/2013/08/government-knocking-doors-because-google-searches/67864/
Boston Marathon Bombing: U.S. Rep. Keating Demands Answers From New FBI Director
In a scathing letter, Massachusetts Congressman William Keating has demanded “forthright information” about the Boston Marathon bombing from the newly confirmed director of the Federal Bureau of Investigation.
Keating, a Cape Cod Democrat, sent the three-page letter to James Comey on Wednesday afternoon, two days after he was confirmed by the Senate to replace Robert Mueller as head of the agency.
“Open questions remain, particularly in regard to inadequate information-sharing, restrictive investigative guidelines/protocols, and an inability to follow up on suspicious activities/travel of individuals residing in the U.S.,” Keating wrote. He added he hopes the FBI would “agree to assist in closing loopholes that may hinder the future identification or capture of dangerous individuals before lives are lost.”...
http://whowhatwhy.com/2013/08/01/boston-marathon-bombing-u-s-rep-keating-demands-answers-from-new-fbi-director/
Keating, a Cape Cod Democrat, sent the three-page letter to James Comey on Wednesday afternoon, two days after he was confirmed by the Senate to replace Robert Mueller as head of the agency.
“Open questions remain, particularly in regard to inadequate information-sharing, restrictive investigative guidelines/protocols, and an inability to follow up on suspicious activities/travel of individuals residing in the U.S.,” Keating wrote. He added he hopes the FBI would “agree to assist in closing loopholes that may hinder the future identification or capture of dangerous individuals before lives are lost.”...
http://whowhatwhy.com/2013/08/01/boston-marathon-bombing-u-s-rep-keating-demands-answers-from-new-fbi-director/
Subscribe to:
Comments (Atom)